Introduction.
The cyber attack on KADOKAWA by the Russian hacker group BlackSuit and the leak of personal information has been a hot topic recently as it has been trending on X.
In this article, I would like to describe the entire cyber attack on KADOKAWA and what we can learn from this case as a reminder.
The full extent of cyber-attacks (ransomware)
| Date and Time | summary |
|---|---|
| 6/8, just after 3:00 a.m. | Nico Douga (1.17 million paying subscribers) experienced problems with users not being able to access videos. →Shortly thereafter, all Nico Douga services were shut down, and part of the e-commerce site and ticket sales service were also disrupted. |
| 6/8, 4:03 p.m. | Hackers contact you demanding 1.5TB of information leak and payment of 1.7 billion yen worth of bitcoins in exchange for the leaked data. |
| 6/9 | KADOKAWA: Consult with outside professional organizations, etc. |
| 6/10-13 | KADOKAWA transfers $2.98 million worth of bitcoin to the hacker’s side. |
| 6/14 | Hackers request additional Bitcoin transfers. |
| 6/17, 4:42 p.m. | Hackers send leaked information and threaten again to expose users’ personal information |
| 6/18 | Explanation of damage at the General Meeting of Shareholders |
| 6/22 | NewsPicks reports on emails exchanged between KADOKAWA Group and perpetrators; KDOKAWA responds that they could facilitate cyber attacks. |
| 6/27 | Dwango announces a damage and recovery plan (which will take at least one month). President Natsuno explained that there was no information leakage. |
| 6/30 | X-Day of ransom payment |
| 7/2 | Hackers begin uploading personal information to the Dark Web. |
First hand KADOKAWA response
According to a NewsPicks scoop, once before June 13, KADOKAWA transferred $2.98 million worth of bitcoins to the hacker’s side, without the consent of its board of directors, according to COO Awata.
As for this initial response.
- Should they have paid the ransom in the first place?
- Was it good that despite being a publicly traded company, it gave some of the funds entrusted to it by its shareholders to criminals as ransom?
and other questionable opinions.
The rest is a bit of an off-the-wall brawl.
- Was NewsPicks right to report the scoop at this time?
- Wouldn’t this encourage crime and violate the press agreement?
Some said that they were not sure what to do with the money.
It is unclear whether this NewsPicks scoop report was the trigger, but KADOKAWA took the firm option of not paying the hacker group an additional ransom demand after all, and on 7/2, the hackers, perhaps because they thought they could not get any more ransom money, went on schedule to upload the personal On 7/27, the hackers uploaded their personal information to the Dark Web as planned.
On 6/27, BlackSuit dared to declare again, “If KADOKAWA does not pay the additional ransom, all data will be released on 7/1,” probably because they were in a hurry that the ransom might not be paid.
What information was leaked?
The details are described in the Twitter timeline here.
- Information on students at N High School and some other KADOKAWA-affiliated educational institutions
- Dwango employees (labor-related documents, my number card, etc.)
- Request form, proposal, and request amount for famous video distributors
- Personal information (real name) of the Vtuber who had a contract with Nico Douga
- Contracts and quotations with suppliers
What should I do if I am attacked by ransomware?
As a general rule, no ransom should be paid.
JPCERT, a private cyber-attack response organization, states that ransoms should not be paid for the following reasons
- No guarantee that files will be restored
- Other damage caused by the cause of damage or infringement has not yet been resolved
- Fear of being victimized by another attack or demand for payment after payment
Basically, it would be better to give up on the data and physically unplug all lines and disconnect all terminals from the Internet first, since it is highly likely that all data in the cloud and backups are also encrypted.
Ransomware Damage Countermeasures
- Keep a backup system.
- With the advance of remote work, more and more employees are able to connect to the corporate network from home, and more and more cases are being targeted there, so ensure password management and completely remove access rights for employees and contractors who have left the company at that point (it may be possible to use an ID management tool such as Okta).
- If there is a VPN connection in place, review the VPN terminal to see if it is vulnerable or using an older model.
- Prepare in advance how the organization should respond in the event of a ransomware attack (like a disaster drill manual).
- Recognize in advance the three major patterns of perceived damage (data becomes unusable, the business system itself goes haywire, or criminals send threatening letters), and respond quickly when an event that fits this pattern actually occurs (basically, physically disconnect all lines first).
Past case: Handa Hospital, Capcom. due to a VPN device.
Handa Hospital in Tsurugi Town, Tokushima Prefecture, was hit by ransomware in October 2021, which encrypted its electronic medical records.
It is highly likely that the ransomware infection route was via a VPN (Virtual Private Network) device manufactured by Fortinet (Fortinet) of the United States. This VPN device had already been exposed to a vulnerability (CVE-2018-13379) that was discovered in 2019, and in September 2021, just before the damage was done, Fortinet announced that authentication information for 87,000 devices had been leaked, and although the leaked list included Handa Hospital, the hospital continued to use the device without notice. The hospital was unaware of the leak and continued to use the system.
Handa Hospital switched to a new version of its electronic medical record system in 2018, but the VPN equipment remained the same, so that was the loophole that caused the damage.

On April 13, 2021, Capcom also revealed that a VPN (Virtual Private Network) device was the cause of the unauthorized access damage it received last November. The demand for teleworking has increased, and when older VPN devices were installed as an emergency response, the said devices were targeted.
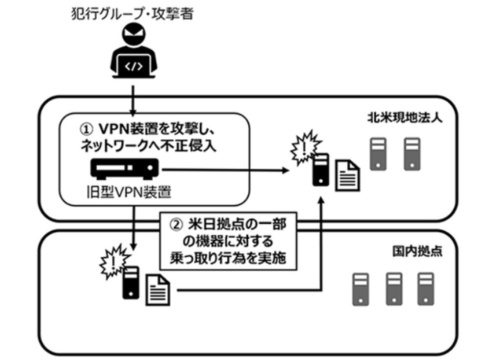

According to the National Police Agency, 63% of the damage in Japan in 2011 was caused by intrusion via a virtual private network (VPN). While the rapid adoption of VPNs has been accompanied by the spread of remote work, poorly managed devices that leave vulnerabilities disclosed by their developers have become easy targets.
It is unclear whether the KADOKAWA case was the same intrusion attempt, but in general, hackers are always looking for vulnerabilities in systems, and this time, they happened to hit KADOKAWA, so they targeted the company.
Also, the following are the obvious things that an individual can do
- Don’t use the same ID password over and over
- MFA (multi-factor authentication) is also required
- Passwords are created with random number generation, 16 digits, etc. (Put in security such as LastPass, 1Password, etc., and change them all to complex passwords. Incidentally, Apple announced its own password management app “Passwords” at WWDC2024 and it will be available from the next OS release.